Product
Pricing
Partners

If you’re an IT professional who manages a Microsoft 365 environment, you probably spend most of your time and effort working toward two basic goals:
When you can manage to pull them both off, it’s a good day, right? And if either of those fail…it’s not such a good day.
Reaching those goals doesn’t just happen by chance, though. There are specific best practices you can follow to greatly increase the likelihood of having a good day. Or week. Or year. Let’s look at five of those best practices, and how CoreView can help with them.
If you were a hacker trying to hack into your system, where would you start? You would probably target your admin accounts, right? That’s because admin accounts have the most privileges. Gartner reports that 80% of all data breaches involve a privileged identity. So, to protect your system from hackers, that’s where you should start too.
Here are some best practices for protecting your accounts.
How many Microsoft 365 admin accounts should your organization have? Spoiler alert: there’s an optimal number, and it’s probably not the number you have.
One is too few, of course, because if that account gets compromised and you lose access to it, you’re in huge trouble. But on the other hand, the more admin accounts you have, the greater the risk of one of them being hacked. Experts generally agree that the optimal number is between two and four. That’s enough to ensure you’ll never be locked out without introducing unnecessary risk.
It’s easier as an admin to just stay logged in with your full-privileged admin account all day long, isn’t it? That way you never have to bother changing accounts. That creates a big security vulnerability, though. You should have a separate, dedicated account just for the administrative activities that require the highest security permissions, and log into it only when needed.
Even if you have the optimal number of admin accounts, and you use them only when needed, there’s still a risk of compromise each time you sign in. Shoulder surfing, keyloggers, network sniffers…you have to assume that bad actors are lurking around every corner. The risks of not doing so are just too great.
Having a strong password might have been enough protection a decade ago, but in today’s security environment, multi-factor authentication is a must. And that second factor shouldn’t be an SMS message or phone call. Use authentication apps, key fobs, or other more secure methods.
Did you know cloud security failures are almost always (99%) the customer’s fault, according to Gartner? That generally means that someone either misconfigured a security policy or failed to consistently apply it throughout the organization. In fact, an IBM study reported that 85% of reported breaches are due to misconfiguration.
So, what causes an IT organization to make costly mistakes like that? The number one thing is lack of visibility. The admins don’t have a way to easily view and manage all the policies, so they don’t see the inconsistencies and security holes until it’s too late.
You can’t really blame IT professionals for missing things. Security policy enforcement can be complicated, involving identities, devices, data, networks, apps, infrastructure, and networks, most of them managed using different consoles. On top of that, IT pros must consider organizational policies and keep up with the latest threat intelligence. The more aspects to a system, and the more users and divisions involved, the greater the risk of making a policy configuration mistake that can open a security vulnerability.
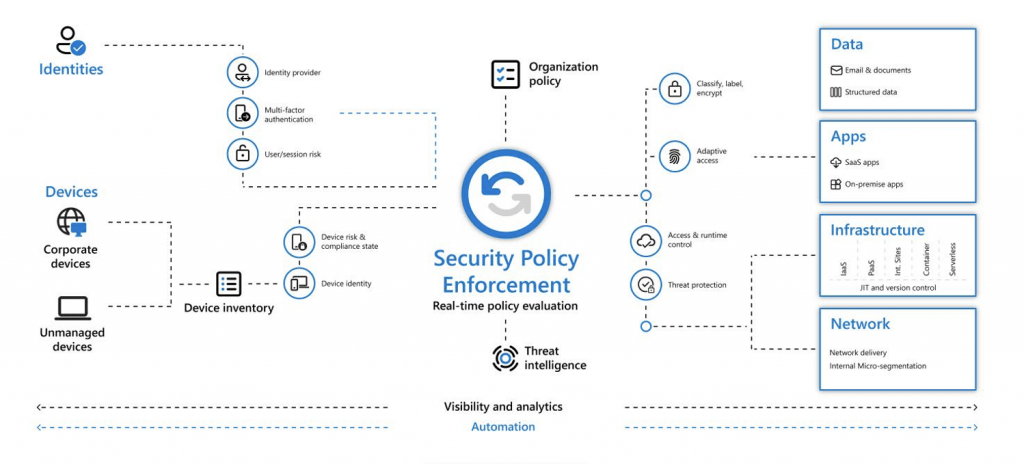
Fortunately, help is available. CoreView provides a single pane of glass view with all user configuration settings. Information from all the consoles is consolidated into a single view.

Here are some more ways that CoreView helps apply, verify, and enforce policies.
CoreView enables you to not only browse security data, but also query it to detect misconfiguration issues before they become a problem. You can easily see when accounts are out of compliance with a policy, such as a user having greater permissions than they should have or lacking a certain license. You can configure alerts to notify you when policy non-compliance is detected, and in most cases, you can repair the misconfiguration with a single click. Talk about a time-saver!
A key component of a robust security policy is to make sure that each account—especially each admin account—has the permissions it needs for the user to get their job done, but not a single privilege more than that. That’s known as the Principle of Least Privilege, or Least Privilege Access. CoreView simplifies this enforcement by increasing visibility and pointing out any anomalies or exceptions that may need looking into.
CoreView also helps with exception management. It’s common to have allowed exceptions to policies in an organization, but those exceptions can create security holes if they aren’t managed correctly. You can configure CoreView to ignore any exceptions that aren’t a concern, so you don’t have to spend time repeatedly approving the same kinds of exceptions, and so you never have to remember why an exception was created or if it is still valid.
CoreView can automate policy enforcement too. You can configure it to either enforce policies automatically or to ask the operator if they want to enforce the policy.
It was commonly thought that requiring users to change their passwords at certain intervals (for example, every 6 months) would decrease the likelihood of password theft. In practice, though, such a policy has unexpected drawbacks. Many users, when forced to change their passwords, try to use a system that they will remember easily, such as changing only one character in their password each time. That defeats the purpose. Having the same time-based password policy across the board is also not the best use of the users’ time because certain accounts are much more attractive hacker targets than others.
CoreView enables you to set up risk-based password management, where each account can be assigned a risk level and a password policy can be configured that applies just to accounts at that level. It also enables risk-based automatic responses to threats, such as logging out, disabling an account, and/or notifying an IT professional.

Is your Microsoft 365 configuration secure enough? (What does “secure enough” even look like?) One way to assess it is to compare your system’s policies to the policies of the Center for Internet Security (CIS) benchmarks for Microsoft 365.
CIS is a non-profit organization that helps organizations implement best security practices. You can download the latest CIS benchmark for security Microsoft Office here.
CIS has worked with Microsoft to create a book called CIS Benchmarks: CIS Microsoft 365 Foundations, a collection of best practices to verify that your security posture is good enough. You can download the book here, read it, and apply its advice to your systems.
There’s a shortcut, though. If you use CoreView, it monitors and can enforce most of the CIS benchmark controls for Microsoft 365 automatically. CoreView also provides a free Microsoft 365 Health Check on their website.
A single-tenant system is convenient and allows full collaboration among all the divisions and departments that use it. Workers achieve maximum productivity under a single-tenant system because they aren’t blocked from accessing anything they need. However, a single-tenant system is more vulnerable to security breaches because everything is there in one big pool.
The alternative is a multi-tenant system, where each department, division, or other group has its own separate Microsoft 365 operating space. A multi-tenant setup gives you total segregation and maximum security, but it limits productivity and collaboration. It also greatly increases the administration and management burden to have multiple separate instances of Microsoft 365, and decreases transparency because admins are constantly switching systems.
A basic best practice is for a company’s IT decision-makers to strategically choose whether to use a single-tenant or multi-tenant organization—and if the latter, to choose how those different tenancies will be grouped or organized.
But wait–what if you didn’t have to choose between security and ease of management? With CoreView, you can segment your single tenant into groupings called virtual tenants. Each virtual tenant can consist of a custom-selected group of users, groups, devices, and even telephone numbers. An administrator can be assigned to work with a certain virtual tenant (or a group of virtual tenants) and can view reports and statuses across all the virtual tenants they are responsible for.
It’s important that everyone has the licenses they need to do their jobs, of course, but what about the other side of that coin? Is every license you are paying for being productively used? Or are some of them languishing, attached to the accounts of users who never use them, or who don’t use them at the level they are authorized for?
It’s estimated that 30% of purchased licenses in organizations are not fully utilized. Many of them are unassigned. For example, the company might purchase 1000 licenses for a product and then only assign them to 600 people, retaining the other 400 licenses in reserve for future use. Having a few extra licenses is all well and good, but if you’re paying for them on a yearly subscription, many extra licenses are just wasted money. Another group of licenses are inactive. Maybe they were assigned to a user account at some point and that user has left the company, for example, or moved into a different role where they no longer use the license. Still, other licenses are oversized for the user they are assigned to. For example, a user who only needs basic Office applications doesn’t need a full-featured license for every product your company deploys.
This kind of inefficiency wastes IT dollars that could be used for something that will provide a return on investment (ROI).
Auditing license usage can be a worthwhile use of an IT professional’s time, but it takes a while. For CoreView users, however, the time needed is minimal because CoreView can provide reports that show you which accounts are inactive or overprovisioned, as well as which licenses are unassigned.

Let’s face it—the average IT professional’s job consists of a significant amount of routine drudgery, like provisioning and deprovisioning user accounts. That’s bad for several reasons. One is that it increases employee turnover. Another is that IT pros get busy, and things start slipping through the cracks. As I talked about in the previous section, a big chunk of the unused licenses in an organization is due to failure to deprovision user accounts on time. That’s not only a waste of license money, but it’s also a security risk.
When deprovisioning an account, you need to go through the onboarding template in reverse! You need to see what this soon-to-be-former employee had when they started and what was added along the way. That will tell you what extra permissions need to be revoked outside of the standard onboarding set, often across multiple platforms and applications.
Here’s a dramatic real-life example. In 2020, a former Cisco employee was able to access the vendor’s IT environment five months after he left the company and delete 456 virtual machines used to run the WebEx Teams application, which cost Cisco $1.4 million to recover from. Why did this happen? Because someone in IT failed to deprovision his account.
With CoreView, you can not only gain insight into the permissions and history of an account, but you can act on multiple accounts based on conditions and approvals. For example, you could have a rule like “delete guest accounts that haven’t been used in the past 60 days, but first get approval from the manager.”
CoreView can automate many kinds of processes, not just provisioning and deprovisioning. Wherever you find a tedious task that drags down IT productivity, CoreView can be configured to perform that task more quickly, reliably, and accurately.
Remember that as a Microsoft 365 admin, you want to ensure that all systems, data, and user accounts are secure, and ensure that everybody has the permissions and licenses they need to do their jobs.
In this article, we reviewed five habits that can help you succeed, and you learned how CoreView can help with them: