Microsoft 365 recovery isn’t one backup tool. It’s layered: data backup, retention/eDiscovery, identity controls, and tenant config restore—so you can recover content and a known-good state.
Inside this article
Executive summary
When it comes to making decisions about backup and recovery for your Microsoft 365 (M365) environment, there isn’t going to be a single product that meets all your needs. This is because it’s about much more than just workload-data for Exchange, SharePoint, OneDrive, and Teams. You need to take into account retention/eDiscovery for compliance preservation; identity controls to reduce blast radius; and tenant configurations when policies, permissions, and security settings change due to mistakes, drift, or attackers. This requires a multi-product layered approach, and this article will help you understand your needs, and map that to the available tools set. Your aim should be to not just ensure you can restore your data, but that you can meet compliance obligations and also be able to restore to a known-good state.
Why Microsoft 365 “backup” is a tool-selection problem
When teams say “we need an M365 backup tool,” they’re usually trying to solve multiple recovery problems with one purchase: restore user content fast, meet compliance obligations, contain identity-driven incidents, and (increasingly) get the tenant’s security configuration back to a known-good state. Those are different outcomes and they map to different tool capabilities.
A practical way to approach this is to think in layers, because each layer answers a different buying question:
- Workload-data backup (Exchange, SharePoint, OneDrive, Teams): Can this tool restore the content my users need to work? (granularity, speed, cross-workload restore, point-in-time)
- Retention/eDiscovery (Purview): Can I prove and preserve data for compliance and legal needs? (holds, immutability, defensible retention)
- Identity controls (Entra ID/privileged access): Can I limit blast radius when an account or admin session is compromised? (least privilege, step-up auth, access review)
- Tenant configuration restore: If policies, permissions, and security settings change, can I get back to a known-good configuration quickly? (baseline, history, rollback)
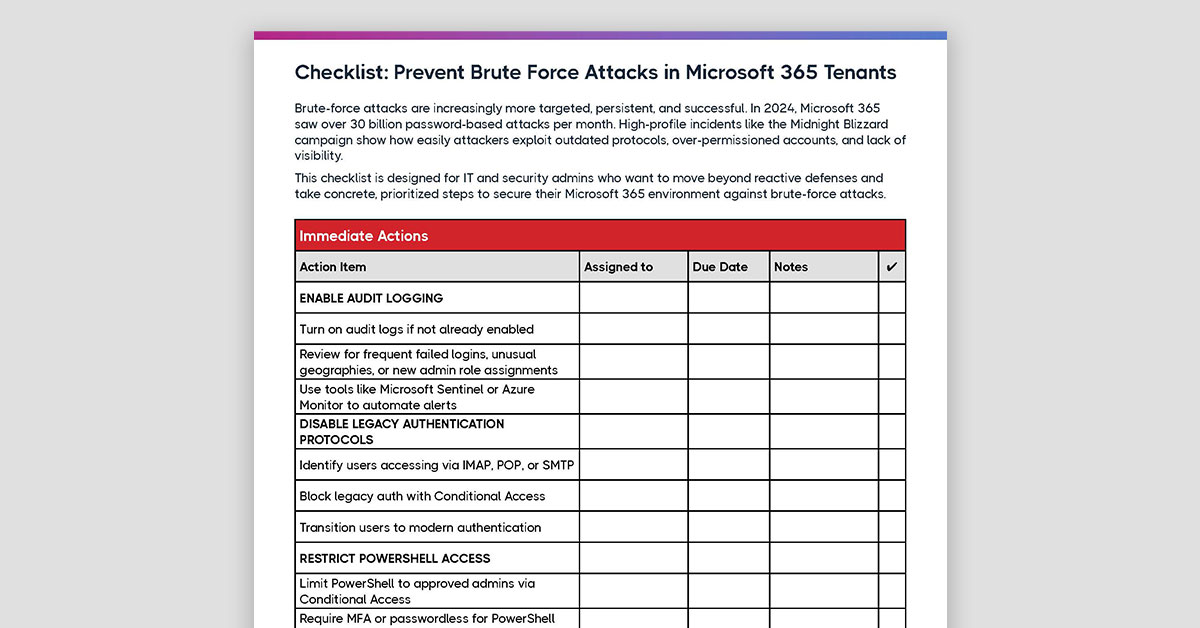
M365 recovery gets complicated for a simple reason: the tenant is bigger than most people treat it. M365 spans 60+ apps and services and 10,000+ configuration settings. So incidents aren’t just “lost files,” they’re often broken access, altered policies, and weakened security posture. Your tool choice should reflect what you actually need to restore: data, access, and configuration state.
The failure modes that should change what you look for in a tool
These aren’t just “threats”, they’re the scenarios that expose whether a product is a true recovery platform or just a point restore utility:
- Ransomware and destructive actions inside M365
How it affects your tool choice: Look for fast bulk restore, restore at scale, and clear reporting. - Account takeover
How it affects your tool choice: Prioritize identity containment (least privilege, role boundaries, access governance) and evidence that the tool can help you recover from security setting changes, not only content loss. - Admin error and automation mistakes at scale
How it affects your tool choice: Evaluate safeguards like change visibility, rollback workflows, and the ability to recover from a bad script/bulk action – especially for policy and permission changes. - Configuration drift (slow posture decay)
How it affects your tool choice: Ask whether the tool can baseline, detect, and roll back configuration changes over time – otherwise you may restore data into a tenant that’s still misconfigured.
Retention vs backup vs restore
On the surface, understanding the difference between retention, backup, and restore may seem obvious, but there are crucial nuances you need to take into account to ensure you don’t get the wrong tool for the job. M365 includes retention and native recovery features. They matter. But during evaluation (and especially during incidents) they’re easy to confuse with “backup.” A clearer way to assess tools is to map each capability to the outcome you need:
Retention (compliance preservation)
Retention is policy-driven preservation for compliance and information governance. It helps you keep data according to rules, holds, and regulatory needs, but it’s not inherently designed as an operational restore system with RPO/RTO guarantees.
Click here to see the Microsoft Purview retention overview: https://learn.microsoft.com/purview/retention
Native recovery (recycle bin, version history, workload features)
Native recovery features cover common mistakes, but they’re scenario-bound and time-bound. This means that at best they should be treated as your “first-aid kit,” not your incident recovery strategy.
For example:
Backup (independent copies and defined restore workflows)
A solid backup approach implies:
- Independent copies
- A clear restore process
- The ability to meet your RPO and RTO
Restore (the real deal)
Restore is where tools are often proven or exposed. Your “backup” needs to deliver:
- Speed
- Granularity
- Confidence
- Repeatability
Without these elements, then you’re not meeting the operational definition for restore that most organizations need during incidents.
When configuration “rewind” is the difference-maker
Use a tenant-configuration restore layer when incidents involve things like:
- Security policy tampering (e.g., auth and access policies changed)
- Privilege/persistence changes (roles, admin assignments, risky settings that keep access open)
- Drift and “slow breakage” (posture degrades over months until something fails an audit or an attack lands)
- Automation mistakes at scale (bulk changes pushed across tenants/workloads)
Top tool categories for Microsoft 365 backup/restore in 2026
There are four main categories to consider when looking at backup and restore tools for M365:
- SaaS backup for Microsoft 365 workload data
- Tenant configuration backup and restore (“rewind”)
- eDiscovery and retention tooling (compliance preservation)
- Identity and access recovery controls (reduce blast radius)
Below, we’ll set out the most common products to consider and what they do and don’t cover.
Category 1: SaaS backup for Microsoft 365 workload data
Best for rapid restore of Exchange Online, SharePoint Online, OneDrive, and Teams content after deletion or ransomware. These tools will typically protect things like your emails, Teams messages, files, and SharePoint documents, all that good stuff.
Where the gap shows up is that many data backup tools offer only partial configuration coverage.
Some of these might offer a very modest amount of configuration back up, but that tends to be limited to some parts Entra, some parts of the ‘who’s who’ aspects of the environment. For specific tenant configuration backup/restore (‘rewind’), see Category 2.
Some of the common tools in this category include:
Veeam Backup for Microsoft 365
What is it: M365–focused backup product that copies M365 workload data (Exchange, SharePoint, OneDrive, Teams) to storage you control for fast restores.
Strengths:
- Strong restore options across core M365 workloads (granular item-level to larger containers)
- Flexible storage targets (appeals to orgs that want control over where backups live)
- Mature ecosystem and operational familiarity in many IT shops
Potential boundaries to consider:
- Primarily workload-data recovery; tenant configuration backup/restore is typically not the core focus
- Can require meaningful planning around storage, retention, and security hardening of the backup platform itself
- Large-scale restore performance depends heavily on architecture and chosen storage
Rubrik Microsoft 365 Backup
What is it: A SaaS-based backup and recovery offering for M365 workload data with enterprise security and governance-oriented design.
Strengths:
- Enterprise-grade security posture and admin controls are typically a key buying driver
- Good reporting/visibility for proving backup coverage and recovery readiness
- Designed for operational simplicity at scale
Potential boundaries to consider:
- Focus is usually on data protection; configuration coverage is commonly limited compared to true tenant-configuration recovery tools
- Cost can be higher than mid-market alternatives depending on scope and retention
- Restore speed at scale still hinges on planning and “incident reality” testing
AvePoint Cloud Backup
What is it: A SaaS backup tool for M365 that protects workload data (Exchange, SharePoint, OneDrive, Teams) and supports common compliance/retention needs.
Strengths:
- Broad M365 workload coverage with straightforward restore workflows
- Often strong in M365 administration-adjacent scenarios (common in digital workplace programs)
- Useful reporting and controls for day-to-day backup operations
Potential boundaries to consider:
- Like most SaaS backup tools, tenant configuration backup is typically not comprehensive
- Teams backup/restore fidelity can vary by platform constraints and product approach
- Larger restores can require careful testing to validate time-to-restore assumptions
Commvault Cloud (Metallic) for Microsoft 365
What is it: Commvault’s cloud-delivered data protection platform, including M365 workload backup and recovery within a broader enterprise backup portfolio.
Strengths:
- Fits well in standardized enterprise backup programs (multi-platform, multi-cloud)
- Strong policy/retention governance patterns for regulated environments
- Good central management when M365 is one piece of a larger backup strategy
Potential boundaries to consider:
- Can be heavier to implement/operate than “M365-only” point solutions
- M365 configuration protection is usually secondary to data protection
- Cost/complexity may be overkill if you only need M365 backup
Cohesity DataProtect (M365 backup)
What is it: Cohesity’s data protection solution with M365 backup capabilities, typically positioned for enterprise-scale backup modernization.
Strengths:
- Strong alignment to large-scale backup modernization programs
- Centralized management approach when protecting multiple data sources beyond M365
- Good for organizations that want consolidation of backup tooling
Potential boundaries to consider:
- May be more platform than you need for “just M365”
- Tenant configuration drift/restore is generally not the primary capability
- Restore-at-scale depends on architecture and operational readiness testing
Druva inSync (Microsoft 365)
What is it: A cloud-native data protection service that includes M365 workload backup as part of a broader SaaS data protection portfolio.
Strengths:
- SaaS delivery model reduces infrastructure overhead
- Simple operational model for backup administration
- Often attractive for distributed orgs that want “set it and manage it” backup
Potential boundaries to consider:
- Typically strongest on data backup; configuration backup/restore is limited
- Advanced recovery scenarios can require careful validation (permissions, structure, fidelity)
- Reporting depth and restore flexibility can vary by licensing/packaging
Barracuda Cloud-to-Cloud Backup
What is it: A SaaS backup tool designed to protect M365 (and other SaaS) workload data with straightforward setup and restore.
Strengths:
- Fast time-to-value and simpler administration for smaller teams
- Good fit for organizations that want a lighter-weight SaaS backup option
- Clear focus on common M365 recovery needs (deleted items, mailbox/file restores)
Potential boundaries to consider:
- Feature depth for complex enterprise recovery scenarios may be more limited
- Configuration coverage is usually modest (typical of this category)
- Scale/performance for very large tenants may require more scrutiny
Keepit (Microsoft 365 backup)
What is it: A SaaS backup and recovery platform for Microsoft 365 that focuses on protecting workload data with a cloud-first operational model.
Strengths:
- SaaS simplicity with comparatively low infrastructure burden
- Designed for quick restores of common M365 content types
- Often straightforward for IT teams to deploy and manage
Potential boundaries to consider:
- Typically not a full solution for tenant configuration backup/restore
- Deep, “forensics-grade” restore requirements (large-scale, complex dependencies) need validation
- As with most SaaS backup, security of admin access and immutability options must be evaluated carefully
N-able Cove
What is it: A cloud-first backup service commonly used by MSPs and IT service providers, with support for Microsoft 365 workload backups as part of a broader backup offering.
Strengths:
- MSP-friendly operations and multi-customer management patterns
- Straightforward deployment for organizations used to provider-managed backup
- Good baseline coverage for common M365 backup needs
Potential boundaries to consider:
- Enterprise-grade requirements (complex governance, highly customized restores) may outgrow the model
- Tenant configuration recovery is generally not the main focus
- Restore-at-scale and detailed reporting should be validated for larger tenants
Restore-first evaluation checklist
Some of the key things you should look for when evaluating these solutions include:
- Workload coverage (Exchange, SharePoint, OneDrive, Teams)
- Restore granularity (item/mailbox/site)
- Speed to restore at scale (incident reality, not a single mailbox)
- Evidence and reporting (prove readiness)
- Security of the backup system itself (admin protections, immutability options)
Category 2: Tenant configuration backup and restore (“rewind”)
Best for restoring tenant configuration state after misconfiguration, drift, or attacker-driven changes. This is the category most organizations realize they’re missing only after something breaks. Most people think Microsoft does this. It doesn’t.
What “configuration restore” looks like in real life
For enteprize grade restore you need two capabilities:
- State restore (known-good tenant posture), and
- Forensics-grade change understanding (what changed, when, and by whom).
After any security events you need to be able to ensure you can not only restore to a previously known safe state for your network, and at the same time be able to figure out what happened. If you can’t do both of these then you’re leaving holes in your defenses.
The most recommended tool is this category is:
CoreView Rewind
What is it: A tenant-configuration backup and restore capability designed to help you capture M365 configuration state and roll back (“rewind”) changes after mistakes, drift, or malicious admin activity.
Strengths:
- Built for state restore of tenant configuration (not just reporting on events)
- Supports “what changed, when, and by whom” with before/after context to guide safe rollback decisions
- Aligns to real incident needs: restore a known-good posture quickly when security settings, policies, or permissions are tampered with
- Designed for M365 operations teams that need repeatable workflows (not bespoke scripting) for configuration recovery
Potential boundaries to consider:
- Not a workload-data backup product (emails/files/Teams messages belong to Category 1 tools)
- Value depends on defining what “known-good” means for your org (baselines/exceptions, restore scope, runbooks)
- As with any restore capability, teams must test scenarios (e.g., Conditional Access policy rollback) to validate operational readiness
Other tools to consider in this category, that don’t necessarily offer the same depth, include:
Quest On Demand for Microsoft 365
What is it: An M365 management platform (with migration/governance/admin capabilities) that’s often used for visibility, administration, and certain change-related workflows across M365.
ManageEngine M365 Manager Plus
What is it: An M365 administration and reporting tool focused on operational management, auditing reports, and delegated admin tasks across common M365 workloads.
AdminDroid
What is it: An M365 reporting and auditing platform designed to give administrators deeper visibility into M365 activity, configuration, and usage through extensive prebuilt reports.
Restore-first evaluation checklist
Some of the key things you should look for when evaluating these solutions include:
- Configuration breadth across workloads (not only identity)
- Baselines and exceptions (approved deviations)
- Change evidence (who/what changed it, and the before/after)
- Restore granularity (single setting/policy vs “everything”)
- Multi-tenant governance and delegated administration options
- Controls to prevent unsafe changes (approvals/workflows where needed)
Category 3: eDiscovery and retention tooling (compliance preservation)
Best for legal hold, regulatory retention, and investigations. Not designed for operational restore aligned to RPO/RTO across workloads. You should treat them as a compliance layer that complements (not replaces) workload-data backup and tenant configuration restore.
Common tools in this category include:
Microsoft Purview (Retention, eDiscovery, Legal Hold)
What is it: Microsoft’s compliance suite for M365 that supports retention policies, holds, content search, and eDiscovery workflows for investigations and regulatory requirements.
Strengths
- Native to M365 (works directly with Exchange, SharePoint, OneDrive, Teams content and compliance signals)
- Strong for preservation use cases: retention policies, litigation hold/legal hold, and defensible collection workflows
- Centralized compliance controls, auditing, and role-based access aligned to M365 governance models
Potential boundaries to consider:
- Built for compliance preservation and discovery – not operational restore with RPO/RTO guarantees
- Hold/retention can preserve content, but it won’t “rewind” tenant configuration, policies, or access controls after an incident
- eDiscovery workflows can be complex and permissions-heavy; success depends on process maturity and scoping discipline
Proofpoint Enterprise Archive
What is it: An enterprise-grade archiving platform (commonly email-focused) designed for long-term retention, supervision, and compliance search to support regulatory and legal requirements.
Strengths
- Strong compliance orientation for regulated industries with mature archive/search requirements
- Commonly used for long-term retention and supervision workflows beyond basic “keep data” needs
- Can reduce reliance on primary mailbox storage for long-term historical access (depending on architecture)
Potential boundaries to consider:
- Primarily a compliance archive – not an operational backup/restore solution for M365 workloads
- Archive search/export does not equal “restore productivity” (RTO) after ransomware or destructive actions
- Does not address tenant configuration/state recovery (policies, permissions, admin changes)
Global Relay Archive
What is it: A regulated communications archiving platform focused on capturing, retaining, and searching communications data for compliance, supervision, and investigations.
Strengths
- Strong fit for highly regulated communications capture/retention requirements
- Emphasis on defensible preservation, search, and supervision workflows
- Often aligned to regulated industry expectations around governance and auditability
Potential boundaries to consider:
- Designed for compliance recordkeeping – not broad Microsoft 365 workload restore
- Restoring business operations after an incident still requires backup/restore tooling and tested runbooks
- Not a tenant configuration recovery solution
Smarsh Enterprise Archive
What is it: An enterprise archive focused on compliant retention, supervision, and eDiscovery of electronic communications across channels, often used in regulated environments.
Strengths
- Strong supervision and compliance features for communications-heavy organizations
- Helps support investigations and regulatory examinations with centralized search and retention
- Useful when compliance scope extends beyond M365 alone (multi-channel communications)
Potential boundaries to consider:
- Archive/eDiscovery ≠ operational restore (RPO/RTO) for M365 workloads
- Archive content is typically for review and production – not rapid restore of user productivity states
- Doesn’t solve tenant configuration rollback or drift recovery
Veritas Enterprise Vault / Veritas Alta Archiving
What is it: Veritas’s archiving solutions for long-term retention, compliance, and search – offered as traditional Enterprise Vault and cloud-delivered options under the Alta portfolio (packaging varies).
Strengths
- Long-standing presence in enterprise archiving with mature retention and search patterns
- Strong fit for orgs standardizing archiving across multiple repositories (beyond M365 in some deployments)
- Can support governance-heavy retention and disposition programs
Potential boundaries to consider:
- Typically oriented to archiving/compliance rather than fast operational restores with defined RPO/RTO
- Can be heavier to implement/manage depending on the deployment model and scope
- Doesn’t address tenant configuration/state recovery for M365
Category 4: Identity and access recovery controls (reduce blast radius)
This isn’t “backup,” but it changes recovery outcomes. The less an attacker can change, the less you must restore.
Examples of common tools in this category include:
Microsoft Entra ID (Conditional Access, Identity Protection, Privileged Identity Management)
What is it: Microsoft’s cloud identity platform for M365, with built-in controls to prevent account takeover, limit privilege, and enforce access policies.
Strengths
- Native integration across Microsoft 365 sign-ins, devices, apps, and admin planes
- Conditional Access enables “policy as the control plane” for MFA, device compliance, location/risk-based access
- Identity Protection adds risk detection signals (e.g., risky users/sign-ins) to drive automated responses
- PIM reduces standing admin privilege via JIT activation, approvals, and time-bound role assignment
Weaknesses
- Policy complexity grows quickly (exceptions, legacy auth, service accounts, “why was access blocked?” troubleshooting)
- Strong outcomes depend on disciplined operational processes (role design, reviews, logging, and testing)
- Not a backup/restore system; it prevents and constrains damage rather than “rolling back” tenant state
Okta (Identity platform)
What is it: A third-party identity provider (IdP) and access management platform used to centralize authentication, SSO, MFA, and lifecycle integrations across cloud apps (including M365).
Strengths
- Strong cross-app SSO/MFA experience for heterogeneous SaaS estates
- Good policy and authentication controls independent of Microsoft-native identity (useful in multi-IdP strategies)
- Mature integrations ecosystem for app access and lifecycle workflows
Potential weaknesses:
- For M365–specific protections, you’ll still rely heavily on Entra signals and configurations
- Additional architecture and operational overhead (two control planes to manage)
- Recovery of M365 identity state (roles, policies, auth methods) still needs explicit planning
Ping Identity (Identity platform)
What is it: An enterprise identity and access management suite (SSO, MFA, federation) often used in complex, regulated, or hybrid identity environments.
Strengths
- Strong for complex federation, legacy/hybrid integrations, and enterprise authentication architectures
- Flexible policy design for large organizations with varied access requirements
- Common fit for regulated industries with demanding identity patterns
Weaknesses
- Can be more complex to implement and operate than “M365-first” approaches
- M365 admin-plane protections still require careful Entra alignment
- Not a “restore” tool; requires complementary backup/monitoring to support identity recovery scenarios
CyberArk (PAM)
What is it: A privileged access management platform focused on securing, brokering, and auditing privileged credentials and sessions (including administrators and high-impact accounts).
Strengths
- Strong controls around privileged credential storage, rotation, and access workflows
- Session monitoring/recording can improve investigations and accountability
- Helps reduce persistent admin exposure (especially for shared/admin accounts and sensitive systems)
Potential weaknesses:
- Deployment and process change can be significant (owners, workflows, integrations)
- Doesn’t replace Entra role governance – often complements it
- Not designed to restore identity configuration; it reduces privilege misuse and improves traceability
BeyondTrust (PAM)
What is it: A privileged access management platform that secures privileged credentials, access paths, and administrative sessions across IT environments.
Strengths
- Strong privileged credential governance and access enforcement
- Helps contain blast radius by reducing unmanaged admin access paths
- Useful for standardizing privileged access workflows and audit evidence
Potential weaknesses:
- Requires adoption across admin teams to deliver value (process friction can slow rollout)
- M365-specific role/policy recovery still requires separate planning and tooling
- Overlap with Entra PIM means you must define clear boundaries (who governs what)
SailPoint (IGA)
What is it: An identity governance and administration platform used for access requests, approvals, certifications (access reviews), and policy-driven role governance.
Strengths
- Strong governance workflows for “who should have access to what” (approvals, reviews, attestations)
- Helpful for proving control effectiveness to auditors (certification evidence)
- Good at scaling joiner/mover/leaver governance across many systems
Potential weaknesses:
- Implementation can be long and integration-heavy
- Doesn’t stop attacks in real time; it governs entitlements over time
- Not a backup/restore tool; it reduces over-permissioning and helps prevent privilege sprawl
Saviynt (IGA)
What is it: An identity governance platform that manages access lifecycle, approvals, certifications, and policy-based controls across cloud and enterprise applications.
Strengths
- Robust governance controls for entitlement management and access reviews
- Strong fit for organizations needing governance across many SaaS and enterprise systems
- Helps reduce “standing access” and entitlement sprawl that increases incident impact
Potential weaknesses:
- Governance programs require sustained process ownership (not just tooling)
- Real-time attack containment still relies on IAM/PAM controls
- Doesn’t provide tenant-configuration rollback; you still need restore planning for identity changes
eDiscovery and retention evaluation checklist
Some of the key things you should look for when evaluating these solutions include:
- Limit standing privilege (just-in-time, approvals)
- Monitor risky sign-ins and privilege changes
- Design and test break glass access
- Treat identity configuration changes as “restore-relevant events”
Why layers matter
One customer told us they hit a reality check during recovery planning: their environment wasn’t just “files and mailboxes.” They had 500TB+ spread across OneDrive, Teams, and mailboxes. Their immediate concern wasn’t only storage—it was how to stand the tenant back up: restore the configuration and identity scaffolding that makes Microsoft 365 usable and secure.
That reframed their buying criteria. Rather than trying to solve everything with a single product, they prioritized tenant configuration and identity restoration first—so core access and services could return to a known-good state before tackling broader user-data protection in a cost- and time-realistic way. When M365 data is measured in hundreds of terabytes, “backup” becomes as much about restore sequencing as it is about storage.
How CoreView helps with M365 tenant configuration backup and “rewind”
Most M365 backup conversations stop at workload data (mailboxes, SharePoint sites, OneDrive files, and Teams content). That’s necessary, but it doesn’t cover you for when the tenant’s security and admin configuration changes (by mistake, drift, or an attacker), the environment can be “up” while still being unsafe or unusable.
CoreView focuses on Microsoft 365 Tenant Resilience: backing up tenant configuration, detecting drift and high-impact changes, and enabling restore (“rewind”) workflows to return the tenant to a known-good operational posture.
CoreView Rewind is the Category 2 layer (in the context of this article). It’s designed to help you recover tenant configuration state when those settings are altered at scale or under pressure.
Again, in the context of positioning for this article, if Category 1 gets you your data back, Category 2 gets your tenant back. In real incidents, you often need both, because restoring content doesn’t automatically restore the controls that make M365 secure and operable.
You should use a SaaS data backup tool to restore content with RPO/RTO-aligned workflows. Use CoreView Rewind to restore tenant configuration state and support forensics-grade rollback decisions, so recovery restores approved posture, not just data.
Ready to improve Microsoft 365 Tenant Resilience with configuration backup and recovery?
Request a demo
FAQs
Does M365 back up my data automatically?
M365 includes availability and workload recovery features, but organizations commonly add independent backup tools to meet their own restore objectives.
Is retention the same as backup?
No. Retention is compliance preservation; backup is operational restore with independent copies and defined workflows. Read more at https://learn.microsoft.com/purview/retention
What does “tenant configuration restore” mean in M365?
It means restoring the settings that control security and administration – policies, permissions, and configuration state – after mistakes, drift, or malicious changes (tampering).
If I have an M365 backup tool, why would I also need configuration restore?
Because incidents often change settings, roles, and policies. Restoring content doesn’t automatically restore tenant posture. Any many of the backup vcendors don’t actually back up configurations.
What’s the biggest hidden risk in M365 recovery planning?
Assuming recovery is only about files and mailboxes, when the harder issue is often proving and restoring tenant configuration state.