The legacy approach to Microsoft security isn’t fit for purpose
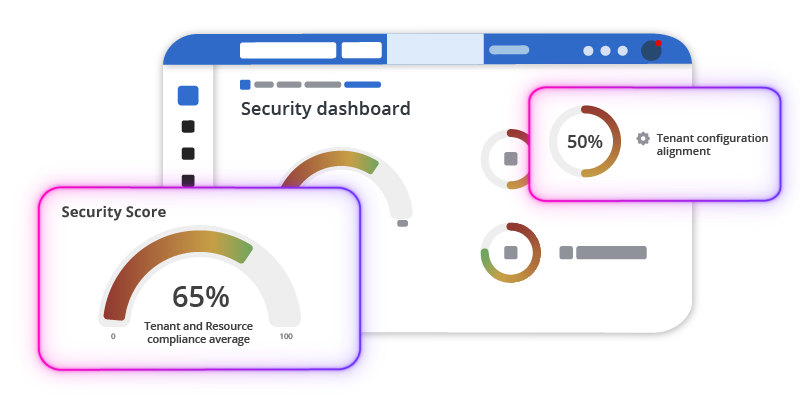
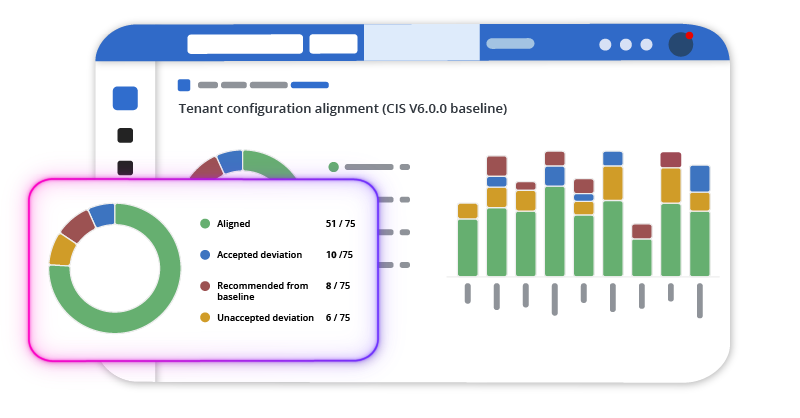
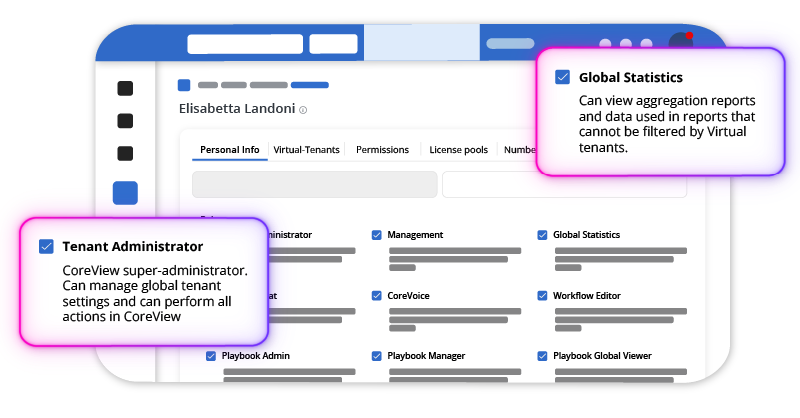
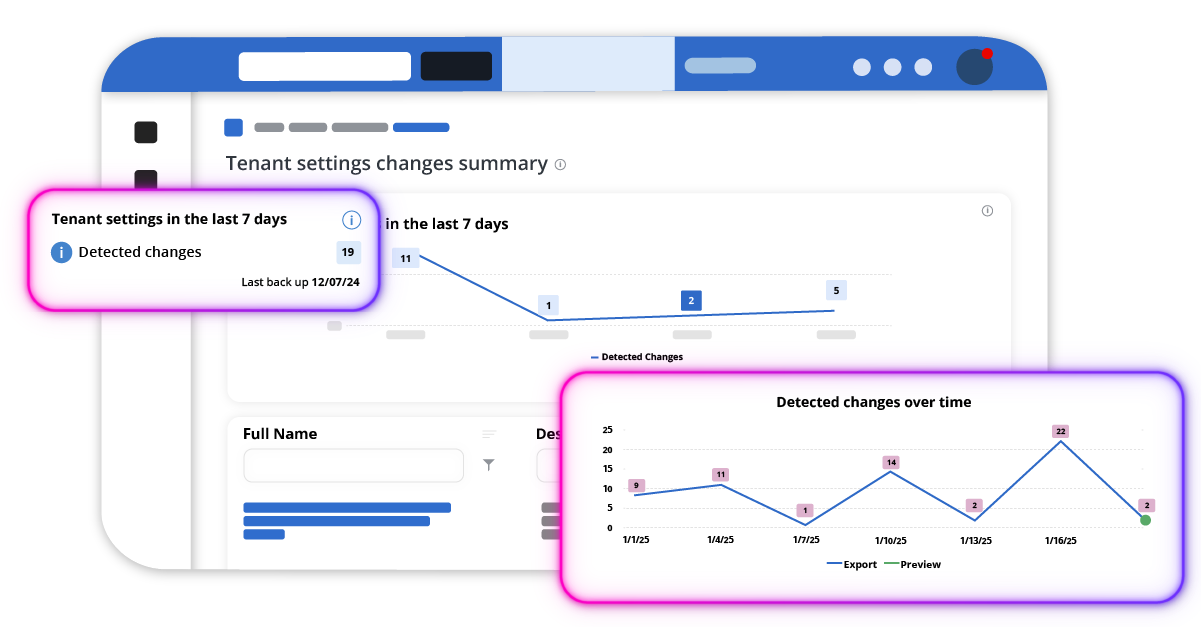
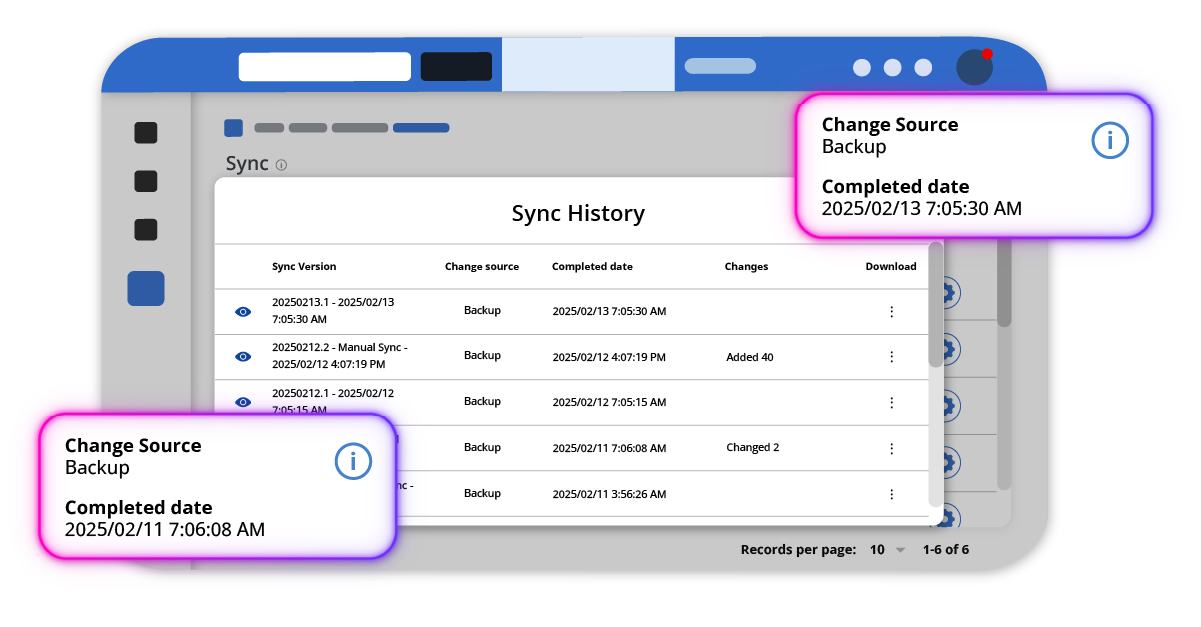
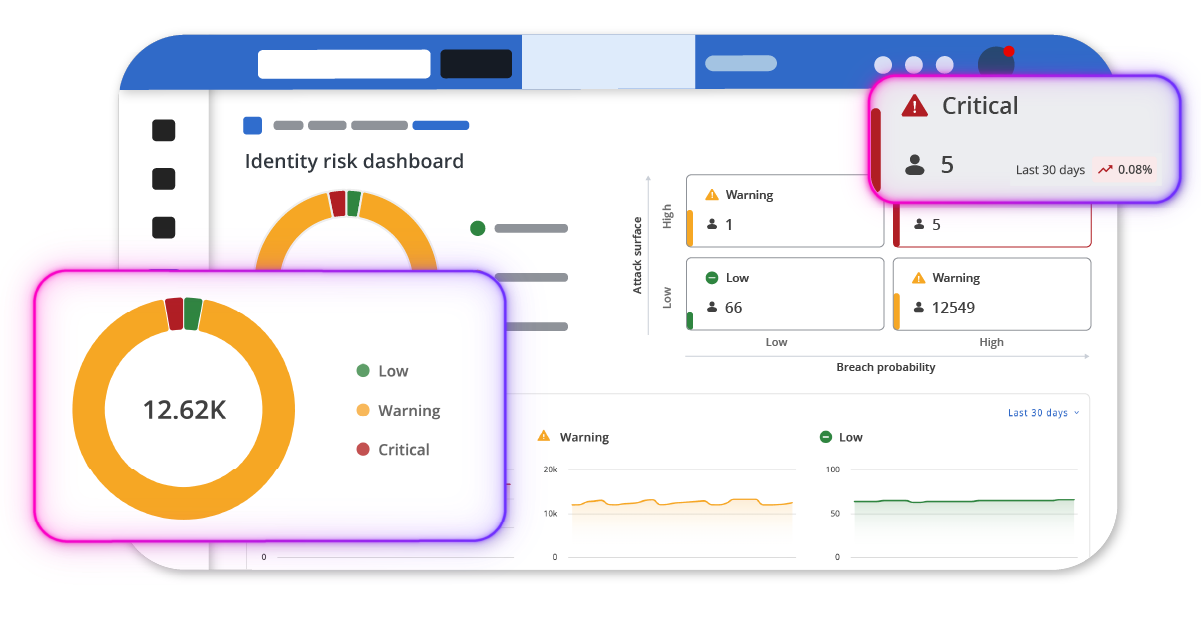
Microsoft 365 is not an app, it’s 60+ interconnected apps & services under relentless attack. Legacy security tools can't keep up. With no visibility of configurations, tenant wide privileges by default, and no tenant configuration backup, it’s time for a new approach.