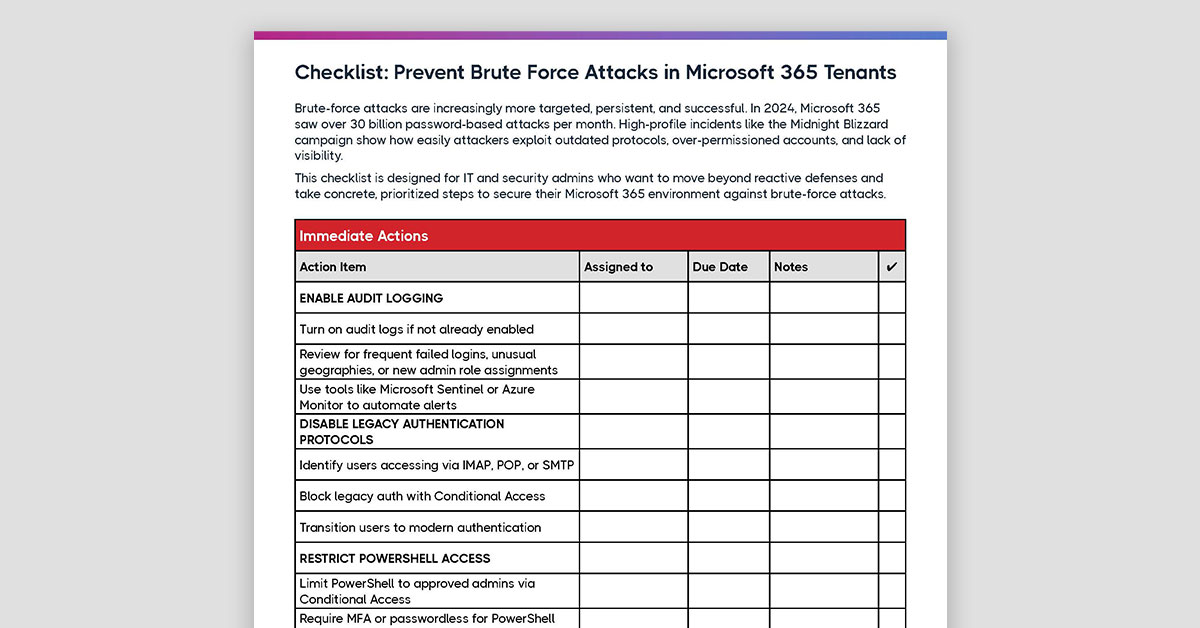
The Microsoft breach by Midnight Blizzard has ignited a flurry of activity across the enterprise IT and cyber security space—and the latest reports suggest this breach may be the tip of the iceberg. That’s why we’ve developed a fast, free PowerShell script to help IT teams check the security of their tenants.
In this article:
Understanding the Microsoft breach attack vector
While the online security community has been watching the Midnight Blizzard fallout for lessons to be learned, it’s clear to anyone that there was no vulnerability here. Attackers found a configuration issue, a simple human error, a forgotten legacy app, a wrong setting, and used it to orchestrate a very complex attack. Microsoft made numerous errors in how they configured their Microsoft 365 tenants—but this isn’t a product defect.
However, these configuration errors are commonplace across enterprise IT and the true scale of the hack may be bigger than currently disclosed. On 26th January 2024, The Washington Post reported ‘more companies expected to disclose email hacks by Russian intelligence’ and that Microsoft themselves had found more victims and was in the process of notifying them.
Microsoft also published detailed guidance for responders on nation-state attack here: https://www.microsoft.com/en-us/security/blog/2024/01/25/midnight-blizzard-guidance-for-responders-on-nation-state-attack/. This piece outlines the nature of the threat, observed techniques, and strategies for mitigation.
From the article: “Threat actors like Midnight Blizzard compromise user accounts to create, modify, and grant high permissions to OAuth applications that they can misuse to hide malicious activity. The misuse of OAuth also enables threat actors to maintain access to applications, even if they lose access to the initially compromised account. Midnight Blizzard leveraged their initial access to identify and compromise a legacy test OAuth application that had elevated access to the Microsoft corporate environment. The actor created additional malicious OAuth applications. They created a new user account to grant consent in the Microsoft corporate environment to the actor controlled malicious OAuth applications. The threat actor then used the legacy test OAuth application to grant them the Office 365 Exchange Online full_access_as_app role, which allows access to mailboxes.”
Verifying your Microsoft 365 tenant security posture
While there’s no real evidence that the breach of Microsoft’s tenant is the cause of the wave of breaches across Microsoft’s customers tenants, IT teams can and should take this opportunity their security posture. We recommend checking some specific, targeted settings immediately. These affect two important, potentially dangerous roles:
- On the Graph side: the AppRoleAssignment.ReadWrite.All MS Graph app role bypasses the consent process. This is by design.
- On the Exchange side: a process or application that's a member of the ApplicationImpersonation role can access the contents of a user's mailbox and act on behalf of that user, even if the user's account is disabled.
Both these roles must be carefully monitored for configuration drift and the potential signs of misuse.
Download the Midnight Blizzard PowerShell tool
While CoreView and Simeon Cloud provide comprehensive tools to manage and secure Microsoft 365 environments, we’ve also created a simple, free PowerShell script to enable everyone to check their security posture.
Download the CoreView App Permissions Scanner to immediately generate:
- From a PowerShell session run each script and follow instructions on screen to login with a Company Administrator:
- AzureADAppsPermissions.ps1
- ExchangeManagementRoles.ps1
- Each script will output 2 files:
- A full list of apps with access to your tenant
- A filtered file with privileges targeted by the Midnight Blizzard group to attack Microsoft 365 tenants
Notes:
- ImportExcel Module is freely distributed with Apache 2.0 license - Copyright of Doug Finke
- Microsoft Graph Beta module is used to get additional information like Publisher Name, not available in V1
Download the tool here.
CoreView offers a set of out-of-the-box playbooks—best practice workflows that help you improve the continuous compliance of your tenant at a resource level. These add an additional check for potential configuration or human errors, which are are the main source of security breaches (95% according to the IBM Cyber Security Intelligence Index Report).
Meanwhile, Simeon Cloud can help you automatically track configuration drift at a tenant level. You can easily detect changes and react promptly, either authorizing them to become part of a new security configuration baseline or identifying them as potential breach and rolling back configuration automatically.